Through the looking glass: On Friday, the otto-js Research Team published an article outlining how users leveraging Google Chrome or Microsoft Edge’s enhanced spelling features may be unknowingly transmitting passwords and personally identifiable information (PII) to third-party cloud-based servers. The vulnerability not only puts the average end user’s private information at risk, but it can also leave an organization’s administrative credentials and other infrastructure-related information exposed to unauthorized parties.
The vulnerability was discovered by otto-js co-founder and Chief Technical Officer (CTO) Josh Summit while testing the company’s script behavior detection capabilities. During the testing, Summit and the otto-js team found that the right combination of features in Chrome’s enhanced spell check or Edge’s MS Editor will unintentionally expose field data containing PII and other sensitive information, sending it back to Microsoft and Google servers. Both features require users to take explicit action to enable them, and once enabled, users are often unaware that their data is being shared with third parties.
In addition to field data, the otto-js team also discovered user passwords might be subject to exposure via the view password option. The option, meant to aid users in ensuring passwords are not incorrectly keyed, inadvertently exposes the password to the third-party servers through the enhanced spell check functions.
Individual users are not the only parties at risk. The vulnerability can result in corporate organizations having their credentials compromised by unauthorized third parties. The otto-js team provided the following examples to show how users logging into cloud services and infrastructure accounts can have their account access credentials unknowingly passed to Microsoft or Google servers.
The first image (above) represents a sample Alibaba Clout Account login. When logging in via Chrome, the enhanced spell check function passes request information to Google-based servers without an administrator’s authorization. As seen in the screenshot below, this request information includes the actual password being entered for the company’s cloud login. Access to this type of information can result in anything from stolen corporate and customer data to the complete compromise of critical infrastructure.
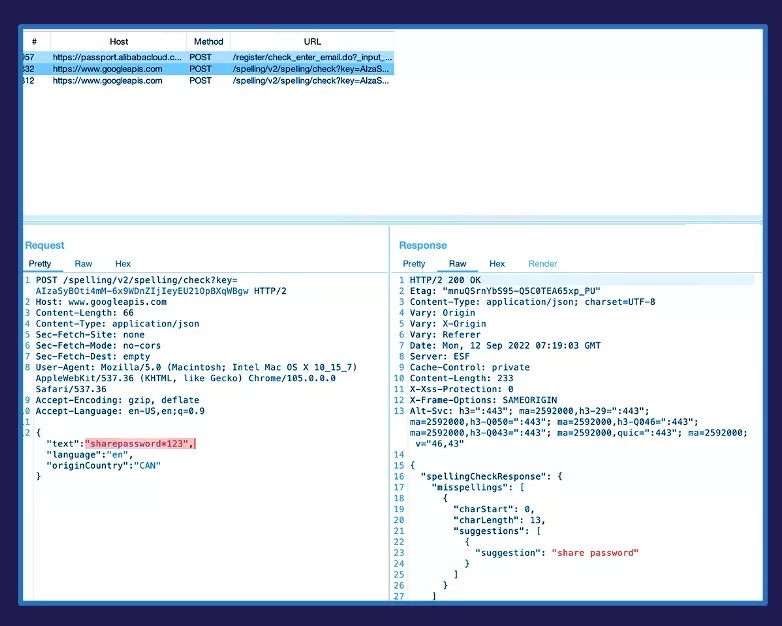
The otto-js team conducted testing and analysis across control groups focused on social media, office tools, healthcare, government, ecommerce, and banking/financial services. More than 96% of the 30 control groups tested sent data back to Microsoft and Google. 73% of those sites and groups tested sent passwords to the third-party servers when the show password option was selected. Those sites and services that did not were the ones that simply lacked the show password function and were not necessarily properly mitigated.
The otto-js team reached out to Microsoft 365, Alibaba Cloud, Google Cloud, AWS, and LastPass, which represent the top five sites and cloud service providers presenting the greatest risk exposure to their corporate customers. According to the security company’s updates, both AWS and LastPass have already responded and indicated that the issue was successfully mitigated.
Image credit: Magnifying Glass by Agence Olloweb; vulnerability screenshots by otto-js


